Ключи в Эфириум с доказательством владения
Последнее обновление страницы: 25 февраля 2026 г.
Ethereum защищает пользовательские активы с помощью криптографии с открытым и закрытым ключами. Публичный ключ используется в качестве основы для адреса Эфириум, то есть он виден широкой публике и используется в качестве уникального идентификатора. Приватный (или "секретный") ключ должен быть доступен только владельцу аккаунта. Приватный ключ используется для "подписи" транзакций и данных, чтобы криптографически можно было доказать, что владелец аккаунта одобряет какое-либо действие определенного приватного ключа.
Ключи Ethereum генерируются с использованием криптографии на эллиптических кривыхopens in a new tab.
Однако когда Ethereum перешел с доказательства работы на доказательство владения, в Ethereum был добавлен новый тип ключа. Первоначальные ключи по-прежнему работают точно так же, как и раньше — не было никаких изменений для ключей на основе эллиптических кривых, защищающих аккаунты. Однако пользователям требовался ключ нового типа для участия в доказательстве владения путем стейкинга ETH и запуска валидаторов. Эта потребность возникла из-за проблем с масштабируемостью, связанных с передачей большого количества сообщений между большим числом валидаторов, что требовало криптографического метода, который можно было бы легко агрегировать, чтобы уменьшить объем обмена данными, необходимый сети для достижения консенсуса.
Этот новый тип ключа использует схему подписи Boneh-Lynn-Shacham (BLS)opens in a new tab. BLS обеспечивает очень эффективную агрегацию подписей, но также допускает извлечение отдельных агрегированных ключей валидаторов и идеально подходит для управления действиями между валидаторами.
Два типа ключей валидатора
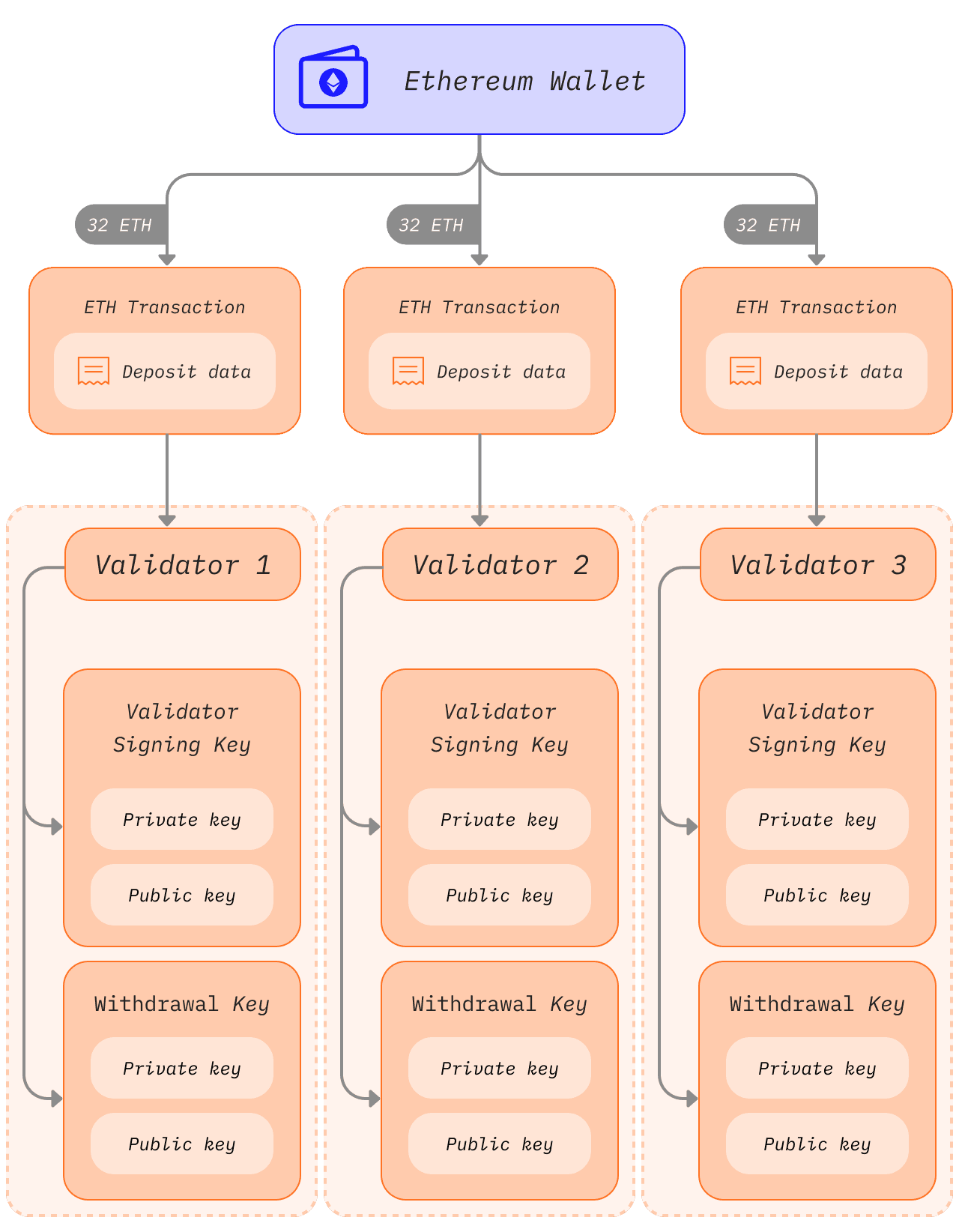
До перехода на доказательство владения у пользователей Эфириум был только один закрытый ключ на основе эллиптической кривой для доступа к своим средствам. С введением доказательства владения пользователям, которые хотели стать соло-стейкерами, также требовались ключ валидатора и ключ для вывода средств.
Ключ валидатора
Ключ подписи валидатора состоит из двух элементов:
- Приватный ключ валидатора
- Публичный ключ валидатора
Назначение приватного ключа валидатора — подписывать он-чейн операции, такие как предложения блоков и аттестации. В связи с этим эти ключи должны храниться в горячем кошельке.
Преимущество такой гибкости заключается в том, что ключи подписи валидатора можно очень быстро перемещать с одного устройства на другое, однако, если они потеряны или украдены, вор может действовать злонамеренно несколькими способами:
- Добиться урезания валидатора:
- Будучи предлагающим блок, подписать два разных блока beacon для одной и той же ячейки
- Будучи аттестатором, подписать аттестацию, которая "окружает" другую
- Будучи аттестатором, подписать две разные аттестации, имеющие одну и ту же цель
- Сделать добровольный выход, который выводит валидатора из стейкинга и предоставляет доступ к его балансу ETH владельцу ключа вывода средств
Публичный ключ валидатора включается в данные транзакции, когда пользователь вносит ETH в депозитный контракт стейкинга. Эти данные известны как данные о депозите и позволяют Ethereum идентифицировать валидатора.
Учетные данные для вывода средств
Каждый валидатор имеет свойство, известное как учетные данные для вывода средств. Это 32-байтное поле начинается либо с 0x00, представляющего учетные данные для вывода средств BLS, либо с 0x01, представляющего учетные данные, указывающие на адрес исполнения.
Валидаторы с 0x00 BLS-ключами должны обновить эти учетные данные, чтобы они указывали на адрес исполнения, для активации выплат избыточного баланса или полного вывода средств из стейкинга. Это можно сделать, указав адрес исполнения в данных депозита во время первоначальной генерации ключа, ИЛИ использовав ключ для вывода средств позже для подписи и трансляции сообщения BLSToExecutionChange.
Ключ для вывода средств
Ключ вывода средств потребуется для обновления данных для вывода средств, чтобы указать адрес для выполнения, если он не был задан при первоначальном депозите. Это позволит начать обработку платежей с избыточным балансом, а также позволит пользователям полностью вывести свои зайстейканные ETH.
Как и ключи валидаторов, ключи для вывода средств также состоят из двух компонентов:
- Приватный ключ для вывода средств
- Публичный ключ для вывода средств
Потеря этого ключа до обновления учетных данных для вывода средств до типа 0x01 означает потерю доступа к балансу валидатора. Валидатор по-прежнему может подписывать аттестации и блоки, поскольку для этих действий требуется закрытый ключ валидатора, однако в случае утери ключей для снятия средств стимул к этому отсутствует.
Отделение ключей валидатора от ключей аккаунта Эфириум позволяет одному пользователю запускать несколько валидаторов.
Примечание: Выход из стейкинга и вывод баланса валидатора в настоящее время требуют подписания сообщения о добровольном выходе (VEM)opens in a new tab с помощью ключа валидатора. Однако EIP-7002opens in a new tab — это предложение, которое в будущем позволит пользователю инициировать выход валидатора и вывести его баланс путем подписания сообщений о выходе с помощью ключа для вывода средств. Это снизит требования к доверию, позволив стейкерам, делегирующим ETH поставщикам услуг стейкинга, сохранять контроль над своими средствами.
Получение ключей из кодовой фразы
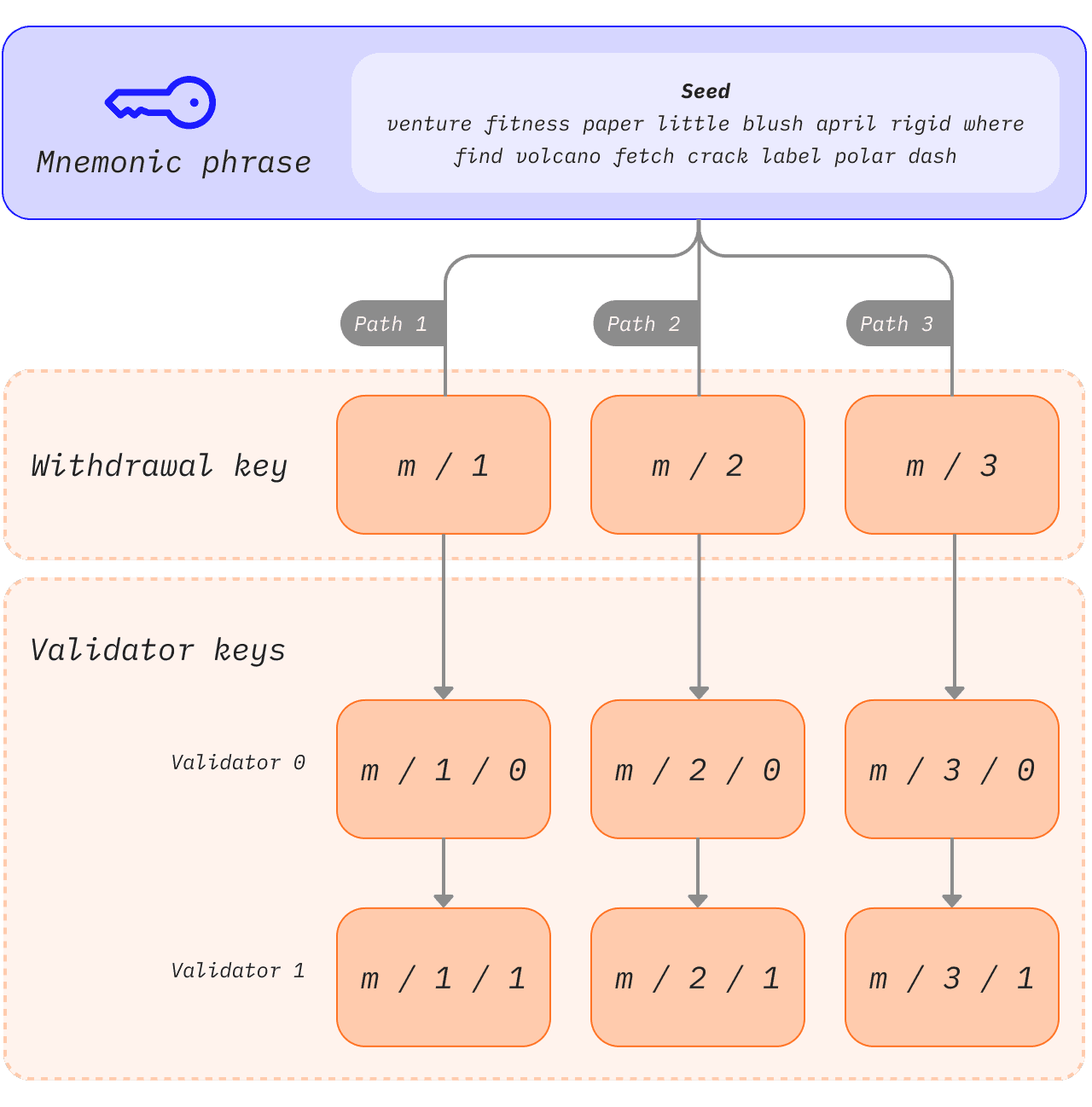
Если бы для каждых застейканных 32 ETH требовался новый набор из 2 полностью независимых ключей, управление ключами быстро стало бы громоздким, особенно для пользователей, у которых запущено несколько валидаторов. Вместо этого несколько ключей валидатора могут быть получены из одной общей сид-фразы, и хранение этой единственной сид-фразы обеспечивает доступ к нескольким ключам валидатора.
Мнемоникиopens in a new tab и пути — это важные функции, с которыми пользователи часто сталкиваются при доступеopens in a new tab к своим кошелькам. Мнемоническая фраза — это последовательность слов, которые действуют как сид для закрытого ключа. В сочетании с дополнительными данными мнемоническая фраза генерирует хэш, известный как "мастер-ключ". Это можно рассматривать как корень дерева. Ветви от этого корня затем могут быть получены с использованием иерархического пути, так что дочерние узлы могут существовать как комбинации хеша их родительского узла и их индекса в дереве. Прочтите о стандартах BIP-32opens in a new tab и BIP-19opens in a new tab для генерации ключей на основе мнемоники.
Эти пути имеют следующую структуру, которая будет знакома пользователям, взаимодействовавшим с аппаратными кошельками:
1m/44'/60'/0'/0`Косые черты в этом пути разделяют компоненты приватного ключа следующим образом:
1master_key / purpose / coin_type / account / change / address_indexЭта логика позволяет пользователям присоединять как можно больше валидаторов к одной мнемонической фразе, поскольку корень дерева может быть общим, а различие может происходить на уровне ветвей. Пользователь может получить любое количество ключей из мнемонической фразы.
1 [m / 0]2 /3 /4[m] - [m / 1]5 \6 \7 [m / 2]Каждая ветвь разделена символом /, поэтому m/2 означает, что нужно начать с мастер-ключа и следовать по ветви 2. На приведенной ниже схеме одна мнемоническая фраза используется для хранения трех ключей вывода средств, каждый из которых имеет два связанных валидатора.