Ethereum सुरक्षा आणि घोटाळा प्रतिबंध
क्रिप्टोकरन्सीमध्ये वाढत्या स्वारस्यामुळे स्कॅमर आणि हॅकर्सकडून वाढता धोका निर्माण झाला आहे. हा लेख हे धोके कमी करण्यासाठी काही सर्वोत्तम पद्धती मांडतो.
लक्षात ठेवा: ethereum.org कडून कोणीही तुमच्याशी कधीही संपर्क साधणार नाही. अधिकृत Ethereum सपोर्टकडून आले आहेत असे सांगणाऱ्या ईमेलला उत्तर देऊ नका.
क्रिप्टो सुरक्षा 101
तुमचे ज्ञान वाढवा
क्रिप्टो कसे कार्य करते याबद्दलच्या गैरसमजांमुळे महागड्या चुका होऊ शकतात. उदाहरणार्थ, जर कोणी ग्राहक सेवा एजंट असल्याचे भासवून तुमच्या प्रायव्हेट कीजच्या बदल्यात हरवलेले ETH परत करू शकतो असे सांगत असेल, तर ते अशा लोकांचा फायदा घेत आहेत ज्यांना हे समजत नाही की Ethereum हे एक विकेंद्रित नेटवर्क आहे ज्यामध्ये अशा प्रकारची कार्यक्षमता नाही. Ethereum कसे कार्य करते याबद्दल स्वतःला शिक्षित करणे ही एक फायदेशीर गुंतवणूक आहे.
वॉलेट सुरक्षा
तुमच्या प्रायव्हेट कीज देऊ नका
कोणत्याही कारणास्तव, तुमच्या प्रायव्हेट कीज कधीही शेअर करू नका!
तुमच्या वॉलेटची प्रायव्हेट की ही तुमच्या Ethereum वॉलेटसाठी एक पासवर्ड आहे. तुमच्या वॉलेटचा पत्ता माहीत असलेल्या व्यक्तीला तुमच्या खात्यातील सर्व मालमत्ता काढून घेण्यापासून रोखणारी ही एकमेव गोष्ट आहे!
तुमच्या सीड फ्रेज/प्रायव्हेट कीजचे स्क्रीनशॉट घेऊ नका
तुमच्या सीड फ्रेज किंवा प्रायव्हेट कीजचे स्क्रीनशॉट घेतल्यास ते क्लाउड डेटा प्रदात्यासोबत सिंक होऊ शकतात, ज्यामुळे ते हॅकर्ससाठी उपलब्ध होऊ शकतात. क्लाउडवरून प्रायव्हेट कीज मिळवणे हे हॅकर्ससाठी एक सामान्य हल्ला करण्याचे माध्यम आहे.
हार्डवेअर वॉलेट वापरा
हार्डवेअर वॉलेट प्रायव्हेट कीजसाठी ऑफलाइन स्टोरेज प्रदान करते. तुमच्या प्रायव्हेट कीज संग्रहित करण्यासाठी ते सर्वात सुरक्षित वॉलेट पर्याय मानले जातात: तुमची प्रायव्हेट की कधीही इंटरनेटला स्पर्श करत नाही आणि तुमच्या डिव्हाइसवर पूर्णपणे स्थानिक राहते.
प्रायव्हेट कीज ऑफलाइन ठेवल्याने हॅक होण्याचा धोका मोठ्या प्रमाणात कमी होतो, जरी हॅकरने तुमच्या कॉम्प्युटरवर नियंत्रण मिळवले तरी.
हार्डवेअर वॉलेट वापरून पहा:
व्यवहार पाठवण्यापूर्वी पुन्हा तपासा
चुकून चुकीच्या वॉलेट पत्त्यावर क्रिप्टो पाठवणे ही एक सामान्य चूक आहे. Ethereum वर पाठवलेला व्यवहार अपरिवर्तनीय आहे. जोपर्यंत तुम्हाला पत्त्याचा मालक माहीत नसेल आणि तुम्ही त्यांना तुमचे फंड परत पाठवण्यासाठी पटवू शकत नाही, तोपर्यंत तुम्ही तुमचे फंड परत मिळवू शकणार नाही.
व्यवहार पाठवण्यापूर्वी नेहमी खात्री करा की तुम्ही ज्या पत्त्यावर पाठवत आहात तो इच्छित प्राप्तकर्त्याच्या पत्त्याशी तंतोतंत जुळतो. स्मार्ट कॉन्ट्रॅक्टशी संवाद साधताना, स्वाक्षरी करण्यापूर्वी व्यवहाराचा संदेश वाचणे ही एक चांगली सवय आहे.
स्मार्ट कॉन्ट्रॅक्टच्या खर्चाची मर्यादा सेट करा
स्मार्ट कॉन्ट्रॅक्टशी संवाद साधताना, अमर्याद खर्चाची मर्यादा देऊ नका. अमर्याद खर्चामुळे स्मार्ट कॉन्ट्रॅक्टला तुमचे वॉलेट रिकामे करता येऊ शकते. त्याऐवजी, खर्चाची मर्यादा केवळ व्यवहारासाठी आवश्यक असलेल्या रकमेपुरती सेट करा.
अनेक Ethereum वॉलेट्स खाती रिकामी होण्यापासून वाचवण्यासाठी मर्यादा संरक्षण देतात.
तुमच्या क्रिप्टो फंडांवर स्मार्ट कॉन्ट्रॅक्टचा ॲक्सेस कसा रद्द करावा
सामान्य घोटाळे
स्कॅमर्सना पूर्णपणे थांबवणे अशक्य आहे, परंतु त्यांच्या सर्वात जास्त वापरल्या जाणाऱ्या तंत्रांबद्दल जागरूक राहून आपण त्यांना कमी प्रभावी बनवू शकतो. या घोटाळ्यांचे अनेक प्रकार आहेत, परंतु ते सामान्यतः समान उच्च-स्तरीय नमुन्यांचे अनुसरण करतात. दुसरे काही नाही, तर लक्षात ठेवा:
- नेहमी संशय बाळगा
- कोणीही तुम्हाला मोफत किंवा सवलतीत ETH देणार नाही
- कोणालाही तुमच्या प्रायव्हेट कीज किंवा वैयक्तिक माहितीची गरज नाही
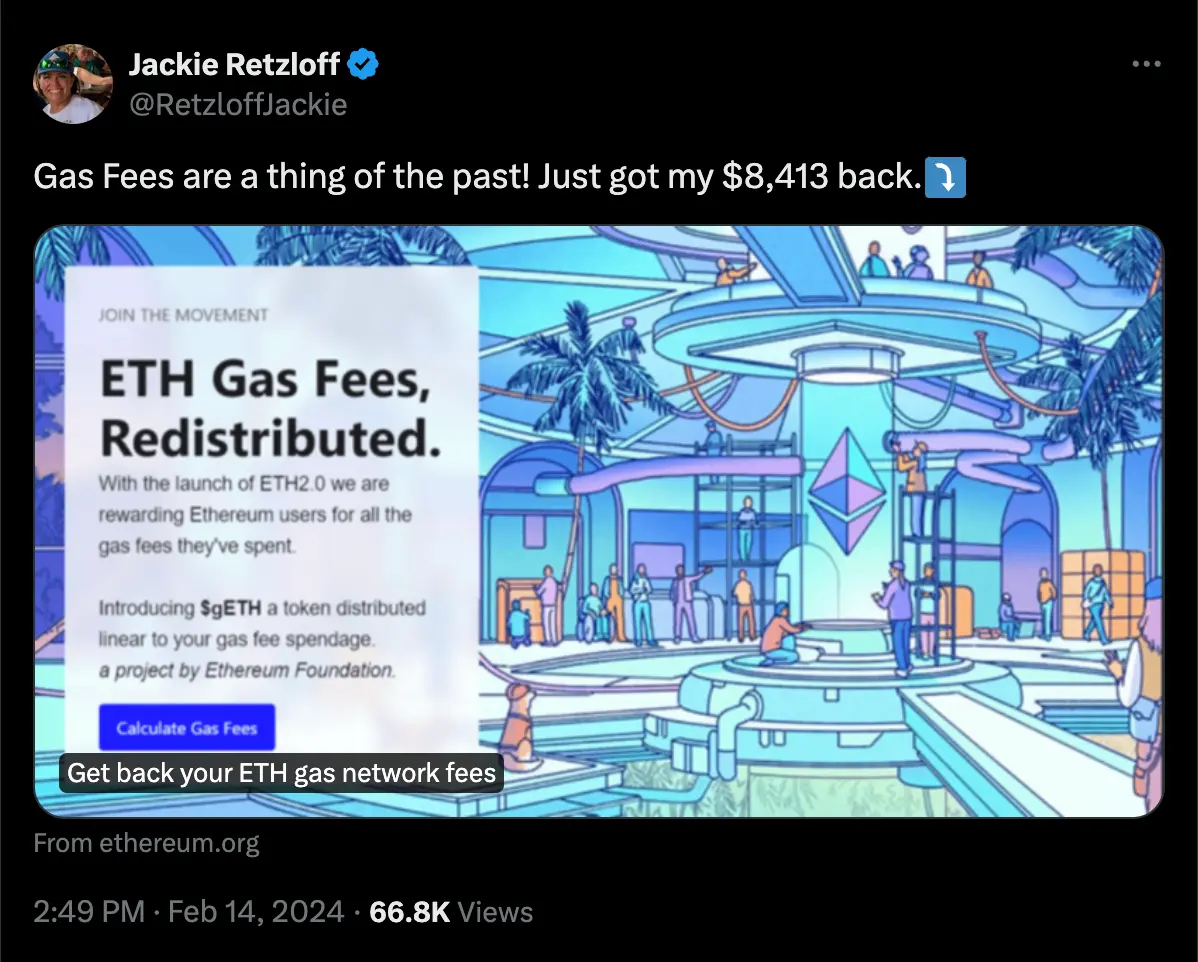
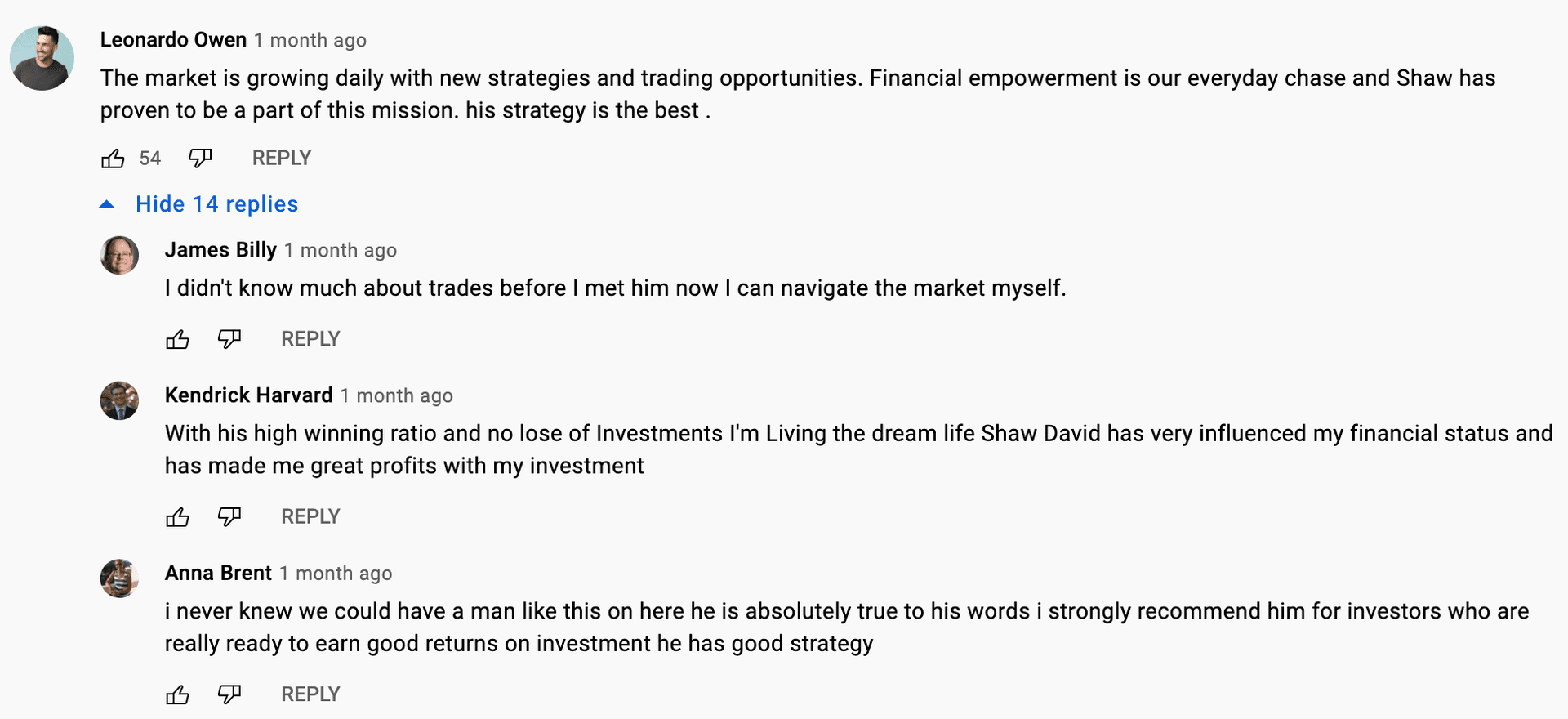
Twitter जाहिरात फिशिंग
Twitter (ज्याला X असेही म्हणतात) च्या लिंक प्रिव्ह्यू वैशिष्ट्याला (अनफर्लिंग) स्पूफ करण्याची एक पद्धत आहे, ज्यामुळे वापरकर्त्यांना ते कायदेशीर वेबसाइटला भेट देत आहेत असा विचार करून फसवले जाऊ शकते. हे तंत्र ट्वीटमध्ये शेअर केलेल्या URL चे प्रिव्ह्यू तयार करण्यासाठी Twitter च्या यंत्रणेचा गैरवापर करते, आणि उदाहरणार्थ (वर दर्शविल्याप्रमाणे) from ethereum.org असे दाखवते, जेव्हा प्रत्यक्षात ते एका दुर्भावनापूर्ण साइटवर पुनर्निर्देशित केले जात असतात.
तुम्ही योग्य डोमेनवर आहात की नाही हे नेहमी तपासा, विशेषतः लिंकवर क्लिक केल्यानंतर.
येथे अधिक माहितीopens in a new tab.
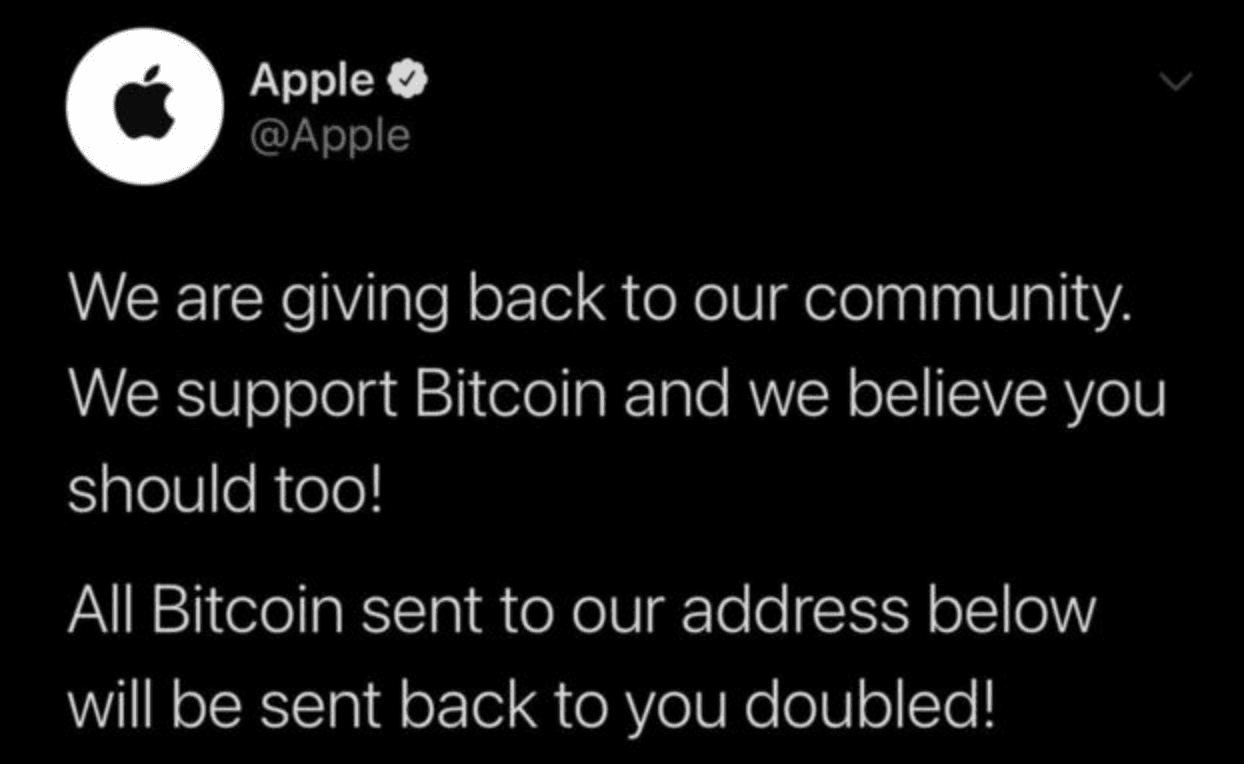
गिव्हअवे घोटाळा
क्रिप्टोकरन्सीमधील सर्वात सामान्य घोटाळ्यांपैकी एक म्हणजे गिव्हअवे घोटाळा. गिव्हअवे घोटाळा अनेक रूपे घेऊ शकतो, परंतु सामान्य कल्पना अशी आहे की जर तुम्ही दिलेल्या वॉलेट पत्त्यावर ETH पाठवले, तर तुम्हाला तुमचे ETH दुप्पट होऊन परत मिळतील.या कारणास्तव, याला 2-फॉर-1 घोटाळा असेही म्हणतात.
हे घोटाळे सामान्यतः गिव्हअवेवर दावा करण्यासाठी मर्यादित वेळेची संधी देतात, जेणेकरून तातडीची खोटी भावना निर्माण होईल.
सोशल मीडिया हॅक
याचा एक हाय-प्रोफाइल प्रकार जुलै 2020 मध्ये घडला, जेव्हा प्रसिद्ध सेलिब्रिटी आणि संस्थांची Twitter खाती हॅक झाली. हॅकरने एकाच वेळी हॅक केलेल्या खात्यांवर Bitcoin गिव्हअवे पोस्ट केला. फसव्या ट्वीट्स लवकर लक्षात आल्या आणि हटवल्या गेल्या असल्या तरी, हॅकर्स तरीही 11 बिटकॉइन (किंवा सप्टेंबर 2021 पर्यंत $500,000) घेऊन पळून जाण्यात यशस्वी झाले.
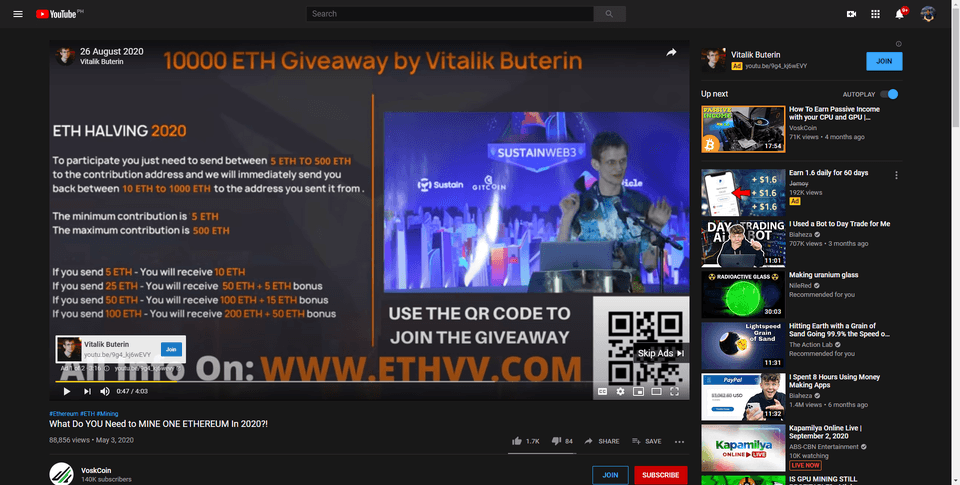
सेलिब्रिटी गिव्हअवे
सेलिब्रिटी गिव्हअवे हे गिव्हअवे घोटाळ्याचे आणखी एक सामान्य रूप आहे. स्कॅमर सेलिब्रिटीने दिलेली रेकॉर्ड केलेली व्हिडिओ मुलाखत किंवा कॉन्फरन्स टॉक घेतील आणि ते YouTube वर लाइव्हस्ट्रीम करतील - जणू काही सेलिब्रिटी क्रिप्टोकरन्सी गिव्हअवेला समर्थन देणारी लाइव्ह व्हिडिओ मुलाखत देत आहे असे भासवतील.
या घोटाळ्यात Vitalik Buterin यांचा सर्वाधिक वापर केला जातो, परंतु क्रिप्टोमध्ये सामील असलेल्या इतर अनेक प्रमुख लोकांचा देखील वापर केला जातो (उदा. Elon Musk किंवा Charles Hoskinson). एखाद्या प्रसिद्ध व्यक्तीचा समावेश केल्याने स्कॅमर्सच्या लाइव्हस्ट्रीमला कायदेशीरपणाची भावना येते (हे संशयास्पद दिसते, परंतु Vitalik यात सामील आहे, त्यामुळे ते ठीक असले पाहिजे!).
गिव्हअवे हे नेहमीच घोटाळे असतात. जर तुम्ही तुमचे फंड या खात्यांवर पाठवले, तर तुम्ही ते कायमचे गमावून बसाल.
सपोर्ट घोटाळे
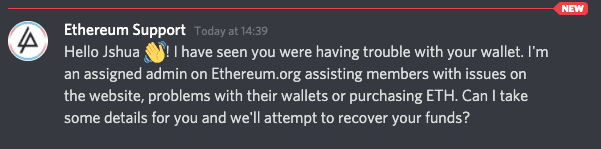
क्रिप्टोकरन्सी हे तुलनेने नवीन आणि गैरसमज असलेले तंत्रज्ञान आहे. याचा फायदा घेणारा एक सामान्य घोटाळा म्हणजे सपोर्ट घोटाळा, जिथे स्कॅमर लोकप्रिय वॉलेट, एक्सचेंज किंवा ब्लॉकचेनसाठी सपोर्ट कर्मचाऱ्यांचे सोंग घेतात.
Ethereum बद्दल बरीच चर्चा Discord वर होते. सपोर्ट स्कॅमर सामान्यतः सार्वजनिक डिस्कॉर्ड चॅनेलमध्ये सपोर्ट प्रश्न शोधून त्यांचे लक्ष्य शोधतात आणि नंतर चौकशी करणाऱ्याला सपोर्ट देणारा खाजगी संदेश पाठवतात. विश्वास निर्माण करून, सपोर्ट स्कॅमर तुम्हाला तुमच्या प्रायव्हेट कीज उघड करण्यासाठी किंवा तुमचे फंड त्यांच्या वॉलेटमध्ये पाठवण्यासाठी फसवण्याचा प्रयत्न करतात.
सर्वसाधारण नियम म्हणून, कर्मचारी तुमच्याशी कधीही खाजगी, अनधिकृत चॅनेलद्वारे संवाद साधणार नाहीत. सपोर्टशी व्यवहार करताना लक्षात ठेवण्यासारख्या काही सोप्या गोष्टी:
- तुमच्या प्रायव्हेट कीज, सीड फ्रेज किंवा पासवर्ड कधीही शेअर करू नका
- कोणालाही तुमच्या कॉम्प्युटरमध्ये रिमोट ॲक्सेस देऊ नका
- संस्थेच्या नियुक्त चॅनेलच्या बाहेर कधीही संवाद साधू नका
'Eth2' टोकन घोटाळा
The Merge च्या आधी, स्कॅमर्सनी 'Eth2' या शब्दाभोवतीच्या गोंधळाचा फायदा घेऊन वापरकर्त्यांना त्यांचे ETH 'ETH2' टोकनसाठी रिडीम करण्यास प्रवृत्त करण्याचा प्रयत्न केला. 'ETH2' असे काहीही नाही, आणि The Merge सह इतर कोणतेही कायदेशीर टोकन सादर केले गेले नाही. The Merge च्या आधी तुमच्या मालकीचे असलेले ETH हे आताचेच ETH आहे. प्रूफ-ऑफ-वर्क पासून प्रूफ-ऑफ-स्टेकवर स्विच करण्यासाठी तुमच्या ETH शी संबंधित कोणतीही कारवाई करण्याची गरज नाही.
स्कॅमर "सपोर्ट" म्हणून दिसू शकतात, आणि तुम्हाला सांगतील की जर तुम्ही तुमचे ETH जमा केले, तर तुम्हाला 'ETH2' परत मिळेल. कोणताही अधिकृत Ethereum सपोर्ट नाही, आणि कोणतेही नवीन टोकन नाही. तुमची वॉलेट सीड फ्रेज कोणाशीही शेअर करू नका.
टीप: असे डेरिव्हेटिव्ह टोकन/टिकर आहेत जे स्टेक केलेल्या ETH चे प्रतिनिधित्व करू शकतात (उदा., Rocket Pool कडून rETH, Lido कडून stETH, Coinbase कडून ETH2), परंतु हे असे काही नाही ज्यावर तुम्हाला "मायग्रेट" करण्याची आवश्यकता आहे.
फिशिंग घोटाळे
फिशिंग घोटाळे हे आणखी एक वाढते सामान्य माध्यम आहे जे स्कॅमर तुमच्या वॉलेटचे फंड चोरण्याचा प्रयत्न करण्यासाठी वापरतील.
काही फिशिंग ईमेल वापरकर्त्यांना अशा लिंक्सवर क्लिक करण्यास सांगतात जे त्यांना बनावट वेबसाइटवर पुनर्निर्देशित करतात, आणि त्यांना त्यांची सीड फ्रेज टाकण्यास, त्यांचा पासवर्ड रीसेट करण्यास किंवा ETH पाठविण्यास सांगतात. इतर तुम्हाला नकळतपणे मालवेअर स्थापित करण्यास सांगू शकतात जेणेकरून तुमचा संगणक संक्रमित होईल आणि स्कॅमर्सना तुमच्या संगणकाच्या फाइल्समध्ये प्रवेश मिळेल.
जर तुम्हाला अज्ञात प्रेषकाकडून ईमेल आला, तर लक्षात ठेवा:
- तुम्ही ओळखत नसलेल्या ईमेल पत्त्यांवरील लिंक किंवा अटॅचमेंट कधीही उघडू नका
- तुमची वैयक्तिक माहिती किंवा पासवर्ड कोणालाही सांगू नका
- अज्ञात प्रेषकांचे ईमेल हटवा
फिशिंग घोटाळे टाळण्याबद्दल अधिकopens in a new tab
क्रिप्टो ट्रेडिंग ब्रोकर घोटाळे
घोटाळेबाज क्रिप्टो ट्रेडिंग ब्रोकर विशेषज्ञ क्रिप्टोकरन्सी ब्रोकर असल्याचा दावा करतात जे तुमचे पैसे घेऊन तुमच्या वतीने गुंतवणूक करण्याची ऑफर देतील. स्कॅमरला तुमचे फंड मिळाल्यानंतर, ते तुम्हाला अधिक फंड पाठवण्यास सांगून तुमची दिशाभूल करू शकतात, जेणेकरून तुम्ही पुढील गुंतवणुकीच्या नफ्यापासून वंचित राहणार नाही, किंवा ते पूर्णपणे गायब होऊ शकतात.
हे फसवणूक करणारे अनेकदा YouTube वर बनावट खाती वापरून 'ब्रोकर'बद्दल वरवर पाहता नैसर्गिक संभाषण सुरू करून लक्ष्य शोधतात. या संभाषणांना कायदेशीरपणा वाढवण्यासाठी अनेकदा जास्त अपव्होट केले जातात, परंतु सर्व अपव्होट बॉट खात्यांमधून आलेले असतात.
तुमच्या वतीने गुंतवणूक करण्यासाठी इंटरनेटवरील अनोळखी लोकांवर विश्वास ठेवू नका. तुम्ही तुमचे क्रिप्टो गमावून बसाल.
क्रिप्टो मायनिंग पूल घोटाळे
सप्टेंबर 2022 पासून, Ethereum वर मायनिंग करणे आता शक्य नाही. तथापि, मायनिंग पूल घोटाळे अजूनही अस्तित्वात आहेत. मायनिंग पूल घोटाळ्यांमध्ये लोक तुमच्याशी न बोलावता संपर्क साधतात आणि दावा करतात की तुम्ही Ethereum मायनिंग पूलमध्ये सामील होऊन मोठा परतावा मिळवू शकता. स्कॅमर दावे करेल आणि जोपर्यंत वेळ लागेल तोपर्यंत तुमच्या संपर्कात राहील. थोडक्यात, स्कॅमर तुम्हाला पटवून देण्याचा प्रयत्न करेल की जेव्हा तुम्ही Ethereum मायनिंग पूलमध्ये सामील होता, तेव्हा तुमची क्रिप्टोकरन्सी ETH तयार करण्यासाठी वापरली जाईल आणि तुम्हाला ETH लाभांश दिला जाईल. त्यानंतर तुम्हाला दिसेल की तुमची क्रिप्टोकरन्सी लहान परतावा देत आहे. हे फक्त तुम्हाला अधिक गुंतवणूक करण्यास प्रवृत्त करण्यासाठी आहे. अखेरीस, तुमचे सर्व फंड अज्ञात पत्त्यावर पाठवले जातील, आणि स्कॅमर एकतर गायब होईल किंवा काही प्रकरणांमध्ये संपर्कात राहील, जसे की अलीकडील एका प्रकरणात घडले आहे.
मुख्य मुद्दा: सोशल मीडियावर तुमच्याशी संपर्क साधून मायनिंग पूलचा भाग होण्यास सांगणाऱ्या लोकांपासून सावध रहा. एकदा तुम्ही तुमचे क्रिप्टो गमावले की, ते गेले.
लक्षात ठेवण्यासारख्या काही गोष्टी:
- तुमच्या क्रिप्टोमधून पैसे कमवण्याच्या मार्गांबद्दल तुमच्याशी संपर्क साधणाऱ्या कोणापासूनही सावध रहा
- स्टेकिंग, लिक्विडिटी पूल किंवा तुमच्या क्रिप्टोमध्ये गुंतवणूक करण्याच्या इतर मार्गांबद्दल तुमचे संशोधन करा
- क्वचितच, अशा योजना कायदेशीर असतात. जर त्या असत्या, तर त्या कदाचित मुख्य प्रवाहात असत्या आणि तुम्ही त्यांच्याबद्दल ऐकले असते.
मायनिंग पूल घोटाळ्यात माणसाने $200k गमावलेopens in a new tab
एअरड्रॉप घोटाळे
एअरड्रॉप घोटाळ्यांमध्ये एक घोटाळेबाज प्रकल्प तुमच्या वॉलेटमध्ये एक मालमत्ता (NFT, टोकन) एअरड्रॉप करतो आणि तुम्हाला एअरड्रॉप केलेली मालमत्ता क्लेम करण्यासाठी एका घोटाळेबाज वेबसाइटवर पाठवतो. क्लेम करण्याचा प्रयत्न करताना तुम्हाला तुमच्या Ethereum वॉलेटने साइन इन करण्यास आणि व्यवहार "approve" करण्यास सांगितले जाईल. हा व्यवहार तुमची पब्लिक आणि प्रायव्हेट कीज स्कॅमरला पाठवून तुमच्या खात्याशी तडजोड करतो. या घोटाळ्याचे एक पर्यायी स्वरूप तुम्हाला स्कॅमरच्या खात्यात फंड पाठवणारा व्यवहार कन्फर्म करण्यास सांगू शकते.
एअरड्रॉप घोटाळ्यांबद्दल अधिकopens in a new tab
वेब सुरक्षा 101
मजबूत पासवर्ड वापरा
80% पेक्षा जास्त खाते हॅक हे कमकुवत किंवा चोरीला गेलेल्या पासवर्डमुळे होतातopens in a new tab. अक्षरे, संख्या आणि चिन्हे यांचे मोठे मिश्रण तुमची खाती सुरक्षित ठेवण्यास मदत करेल.
एक सामान्य चूक म्हणजे काही सामान्य, संबंधित शब्दांचे मिश्रण वापरणे. असे पासवर्ड असुरक्षित असतात कारण ते डिक्शनरी अटॅक नावाच्या हॅकिंग तंत्राला बळी पडतात.
कमकुवत पासवर्डचे उदाहरण: CuteFluffyKittens!
मजबूत पासवर्डचे उदाहरण: ymv\*azu.EAC8eyp8umf
आणखी एक सामान्य चूक म्हणजे असे पासवर्ड वापरणे जे सोशल इंजिनीअरिंगopens in a new tab द्वारे सहजपणे ओळखले जाऊ शकतात किंवा शोधले जाऊ शकतात. तुमच्या पासवर्डमध्ये तुमच्या आईचे माहेरचे नाव, तुमच्या मुलांची किंवा पाळीव प्राण्यांची नावे किंवा जन्मतारीख यांचा समावेश केल्याने हॅक होण्याचा धोका वाढेल.
चांगल्या पासवर्ड पद्धती:
- तुमचा पासवर्ड जनरेटर किंवा तुम्ही भरत असलेल्या फॉर्मद्वारे परवानगी असेल तितके मोठे पासवर्ड बनवा
- अपरकेस, लोअरकेस, संख्या आणि चिन्हे यांचे मिश्रण वापरा
- तुमच्या पासवर्डमध्ये कुटुंबाची नावे यासारखे वैयक्तिक तपशील वापरू नका
- सामान्य शब्द टाळा
मजबूत पासवर्ड तयार करण्याबद्दल अधिकopens in a new tab
प्रत्येक गोष्टीसाठी युनिक पासवर्ड वापरा
डेटा ब्रीचमध्ये उघड झालेला मजबूत पासवर्ड आता मजबूत पासवर्ड राहत नाही. वेबसाइट Have I Been Pwnedopens in a new tab तुम्हाला तुमची खाती कोणत्याही सार्वजनिक डेटा ब्रीचमध्ये सामील होती की नाही हे तपासण्याची परवानगी देते. जर ती असतील, तर ते पासवर्ड ताबडतोब बदला. प्रत्येक खात्यासाठी युनिक पासवर्ड वापरल्याने, तुमचा एखादा पासवर्ड तडजोड झाल्यास, हॅकर्सना तुमच्या सर्व खात्यांमध्ये प्रवेश मिळण्याचा धोका कमी होतो.
पासवर्ड मॅनेजर वापरा
तुमच्या प्रत्येक खात्यासाठी मजबूत, युनिक पासवर्ड लक्षात ठेवणे आदर्श नाही. पासवर्ड मॅनेजर तुमच्या सर्व पासवर्डसाठी एक सुरक्षित, एन्क्रिप्टेड स्टोअर ऑफर करतो ज्यामध्ये तुम्ही एका मजबूत मास्टर पासवर्डद्वारे प्रवेश करू शकता. नवीन सेवेसाठी साइन अप करताना ते मजबूत पासवर्ड देखील सुचवतात, त्यामुळे तुम्हाला स्वतःचा तयार करण्याची गरज नाही. अनेक पासवर्ड मॅनेजर तुम्हाला हे देखील सांगतील की तुम्ही डेटा ब्रीचमध्ये सामील झाला आहात का, ज्यामुळे तुम्हाला कोणत्याही दुर्भावनापूर्ण हल्ल्यांपूर्वी पासवर्ड बदलता येतात.
पासवर्ड मॅनेजर वापरून पहा:
- Bitwardenopens in a new tab
- KeePassopens in a new tab
- 1Passwordopens in a new tab
- किंवा इतर शिफारस केलेले पासवर्ड मॅनेजरopens in a new tab पहा
टू-फॅक्टर ऑथेंटिकेशन वापरा
तुम्हाला कधीकधी युनिक पुराव्यांद्वारे तुमची ओळख प्रमाणित करण्यास सांगितले जाऊ शकते. यांना फॅक्टर म्हणून ओळखले जाते. तीन मुख्य फॅक्टर आहेत:
- तुम्हाला माहीत असलेली एखादी गोष्ट (जसे की पासवर्ड किंवा सुरक्षा प्रश्न)
- तुम्ही असलेली एखादी गोष्ट (जसे की फिंगरप्रिंट किंवा आयरीस/फेशियल स्कॅनर)
- तुमच्या मालकीची एखादी गोष्ट (तुमच्या फोनवरील सिक्युरिटी की किंवा ऑथेंटिकेशन ॲप)
टू-फॅक्टर ऑथेंटिकेशन (2FA) वापरल्याने तुमच्या ऑनलाइन खात्यांसाठी एक अतिरिक्त सुरक्षा फॅक्टर मिळतो. 2FA हे सुनिश्चित करते की केवळ तुमचा पासवर्ड असणे खाते ॲक्सेस करण्यासाठी पुरेसे नाही. सर्वात सामान्यपणे, दुसरा फॅक्टर हा एक रँडमाइज केलेला 6-अंकी कोड असतो, ज्याला टाइम-बेस्ड वन-टाइम पासवर्ड (TOTP) म्हणून ओळखले जाते, जो तुम्ही Google Authenticator किंवा Authy सारख्या ऑथेंटिकेटर ॲपद्वारे ॲक्सेस करू शकता. हे "तुमच्या मालकीची एखादी गोष्ट" फॅक्टर म्हणून काम करतात कारण टाइम्ड कोड जनरेट करणारा सीड तुमच्या डिव्हाइसवर संग्रहित असतो.
सिक्युरिटी कीज
सिक्युरिटी की हा 2FA चा अधिक प्रगत आणि सुरक्षित प्रकार आहे. सिक्युरिटी कीज हे भौतिक हार्डवेअर ऑथेंटिकेशन डिव्हाइस आहेत जे ऑथेंटिकेटर ॲप्सप्रमाणे काम करतात. सिक्युरिटी की वापरणे हा 2FA चा सर्वात सुरक्षित मार्ग आहे. यापैकी अनेक कीज FIDO Universal 2nd Factor (U2F) मानकाचा वापर करतात. FIDO U2F बद्दल अधिक जाणून घ्याopens in a new tab.
2FA वर अधिक पहा:
ब्राउझर एक्स्टेंशन अनइन्स्टॉल करा
ब्राउझर एक्स्टेंशन, जसे की Chrome एक्स्टेंशन किंवा Firefox साठी ॲड-ऑन्स, ब्राउझरची कार्यक्षमता सुधारू शकतात परंतु धोक्यांसह येतात. डीफॉल्टनुसार, बहुतेक ब्राउझर एक्स्टेंशन 'साइट डेटा वाचण्यासाठी आणि बदलण्यासाठी' ॲक्सेस मागतात, ज्यामुळे ते तुमच्या डेटासह जवळजवळ काहीही करू शकतात. Chrome एक्स्टेंशन नेहमी आपोआप अपडेट होतात, त्यामुळे पूर्वी सुरक्षित असलेले एक्स्टेंशन नंतर दुर्भावनापूर्ण कोड समाविष्ट करण्यासाठी अपडेट होऊ शकते. बहुतेक ब्राउझर एक्स्टेंशन तुमचा डेटा चोरण्याचा प्रयत्न करत नाहीत, परंतु तुम्हाला हे माहित असले पाहिजे की ते करू शकतात.
सुरक्षित राहा:
- केवळ विश्वसनीय स्रोतांमधून ब्राउझर एक्स्टेंशन स्थापित करा
- न वापरलेले ब्राउझर एक्स्टेंशन काढून टाका
- ऑटो-अपडेट थांबवण्यासाठी Chrome एक्स्टेंशन स्थानिकरित्या स्थापित करा (प्रगत)
ब्राउझर एक्स्टेंशनच्या धोक्यांबद्दल अधिकopens in a new tab
पुढील वाचन
वेब सुरक्षा
- मालवेअर-युक्त Chrome आणि Edge ॲड-ऑन्समुळे 3 दशलक्ष पर्यंत डिव्हाइस संक्रमितopens in a new tab - Dan Goodin
- एक मजबूत पासवर्ड कसा तयार करावा — जो तुम्ही विसरणार नाहीopens in a new tab - AVG
- सिक्युरिटी की म्हणजे काय?opens in a new tab - Coinbase
क्रिप्टो सुरक्षा
- स्वतःचे आणि आपल्या निधीचे संरक्षण करणेopens in a new tab - MyCrypto
- सामान्य क्रिप्टो कम्युनिकेशन सॉफ्टवेअरमधील सुरक्षा समस्याopens in a new tab - Salus
- डमी आणि हुशार लोकांसाठी देखील सुरक्षा मार्गदर्शकopens in a new tab - MyCrypto
- क्रिप्टो सुरक्षा: पासवर्ड आणि ऑथेंटिकेशनopens in a new tab - Andreas M. Antonopoulos
घोटाळा शिक्षण
- मार्गदर्शक: घोटाळा टोकन कसे ओळखावे
- सुरक्षित राहणे: सामान्य घोटाळेopens in a new tab - MyCrypto
- घोटाळे टाळणेopens in a new tab - Bitcoin.org
- सामान्य क्रिप्टो फिशिंग ईमेल आणि संदेशांवरील Twitter थ्रेडopens in a new tab - Taylor Monahan
तुमच्या Ethereum ज्ञानाची चाचणी घ्या
पृष्ठ अखेरचे अद्यतन: १४ फेब्रुवारी, २०२६